On New Year’s Day, I received my CanoKey Pigeon which I bought at the end of last year.
Update on 3 January:
I finally received my Canokeys which I have been waiting for a long time. Here is a brief review of it, I won’t go into details of how to use every feature, you can refer to other people’s guides on Yubikeys for most of the usage.
If you don’t know what the hardware key like Yubikey, Canokey or similar, you can start with Zenithal H ’s blog post “From the Ant Design GitHub theft case: Is there an available 2FA in China” (Chinese only) and public talk “CanoKey Applications, Code and Implementation” (Chinese only) to get some introductions.

OpenPGP
This is what I use most at the moment, to sign my commits and to keep my ssh private key. Currently Canokey is going to be a backup key, so I need to import my GPG key into it.
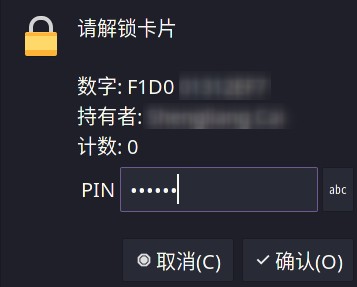
So let’s back up the current ~/.gnupg, then disconnect the internet and gpg --import import the private key we saved before. Then keytocard will write the private key to the card.
Tip
If you are a new user, you can either generate a pair of keys locally and write the subkeys to the card, or you can generate them directly on the card, but you cannot remove them for backup.
Note that the RSA4096 key cannot be generated directly on the card.
But there is a problem here, gpg will record the relationship between the local private key and the smart card number, and only one card can be recorded. This results that I have inserted one card, but I am prompted to insert another card.
This can be solved at this point by using this command.
gpg-connect-agent "scd serialno" "learn --force" /byeNote
gpg 2.3 has multi-card support.
Good, but Arch hasn’t been updated yet (
As for the OpenKeyChain on my Android phone, I plugged it in and it worked straight away.
FIDO2
Use systemd-cryptenroll for laptops to unlock full disk encryption, and systemd-homed for desktops to unlock /home and WebAuthn/FIDO2 for accounts such as Github and Google. Both Yubikey and Canokey work fine with the above features.
However,
systemdis not very robust at the moment, as it cannot register multiple FIDO2 devices 1,nor can it automatically fall back to entering the password 2 when the key is not found at boot (the only way to enter the password to unlock is to remove the fido2 parameter, you need to add an extra boot entry). The automatic fallback to the input password is supported in systemd 250, see here for a solution.
OATH (TOTP)
You can use Yubico Authenticator on your computer, just turn on Custom reader in the settings to support Canokey.
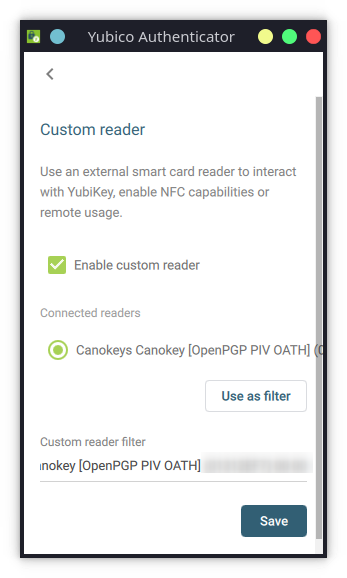
Canokey is ignored on Android phones due to the ID whitelisting of the USB, but group member @xierch has provided a patch that adds Canokey support.
Click To Expand
It works fine for reading and writing TOTPs using USB. A pre-compiled version has been provided by group member @SparrowHe.
Info
Update on 4 January
Today, after fixing the NFC function, I tested the Google Play version and it works with NFC, but because the USB has an ID whitelist, it doesn’t work, so I need to use the patched version above, but my Mi 10S seems to have some problems with this version of NFC, and some of group member reported that the patched version of USB and NFC both work fine. ……
NDEF
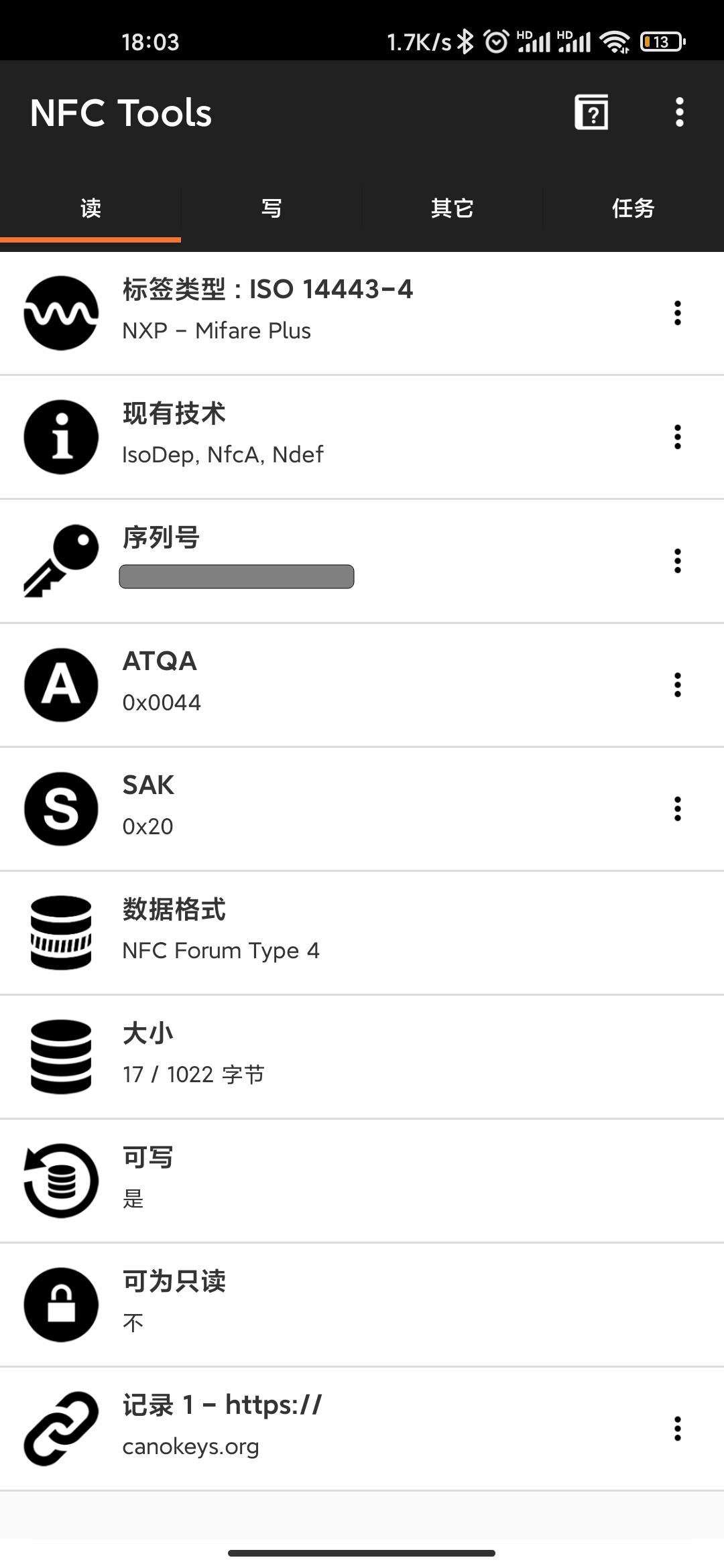
Although I don’t have a use case for this yet, I did test this function in passing when NFC was available and NFC Tools can read and write NDEF information normally.

Summary
The functions that have been tested so far and the software used are as follows.
| USB | NFC | |
|---|---|---|
| FIDO2 | 👍 | 👍 |
| OpenPGP | 👍 | 👎 |
| PIV | ❓ | ❓ |
| NDEF | N/A | 👍 |
| OATH | 👍 | 👍 |
| Arch Linux | Xiaomi Mi 10S (thyme) | |
|---|---|---|
| FIDO2 | systemd 250-4 | WebAuthn - FIDO2 Example 4.2.1 |
| OpenPGP | gnupg 2.2.32-2 | OpenKeychain: Easy PGP 5.7.5 |
| NDEF | N/A | NFC Tools 8.6.1 |
| OATH | yubioath-desktop 5.1.0-2 | Yubico Authenticator 2.2.0 |
Since I don’t have a PIV scenario at the moment, I haven’t tested this feature yet.
Overall, the Canokey Pigeon pretty much covers my current Yubikey 5 NFC usage scenarios, (none of them have Type-C support, so you need to buy an adapter separately), with a few issues to be resolved.
NFC
The NFC performance of CanoKey Pigeon is not really comparable to YubiKey due to the limitation of power consumption of the chip.
I have used Yubikey’s NFC before without any obstacles, but I have not been able to use this Canokey successfully so far, probably because of my posture. I’m not sure how to use it.
But it was fixed after a group member gave me a APDU code , you can refer to the official usage advice and repair guide (Chinese only).
“NFC is really easy to identify when you find the key point”
-- a group member who wishes to remain anonymous
Info
Update on 4 January
Today I successfully used NFC on my phone to complete two-step authentication for Github and Twitter, and I also successfully used NFC for TOTP reading on Yubico Authenticator.
Web Console
Most settings can be managed on the Web Console . Note that Firefox does not support WebUSB3, so you may need to install an additional Chromium.
If you’re using Linux like me, you’ll probably get a device busy error because the gpg-agent is fighting with it. All you have to do is killall gpg-agent and you’ll be fine.
The Web Console does not currently support adding or removing OATH (TOTP/HOTP), you need to use another tool to write to it.
Note
This function is being done.jpg
Until then please use ykman or yubico authenticator
The ykman command requires the -r canokey parameter to specify the reader. openPGP related settings can also be done directly with gpg --edit-card.
